- Used Space Encryption or Pre-Provisioning BitLocker.
- Full Disk Encryption (FDE) or the normal way.
FDE as the name suggests, encrypts the entire disk. Also it's a time consuming process even if configured as a part of OS deployment. It might take 2-3 hours or more depending on the size of the HDD and the size of the data on the HDD. But most people prefer this method.
I will share my experience & task sequences which worked for me to do above in both ways.
SCCM Task Sequence can pre-provision BitLocker if the OS is Windows 7 or above and the device has a TPM. So what's the big deal here? ...Actually here we have MBAM (Microsoft BitLocker Administration & Monitoring) - part of MDOP. If MBAM is on picture, entire BitLocker related things managed by it. Recovery keys, GPO, TPM Passwords, reports and so on. If MBAM is integrated with SCCM, BitLocker Compliance Reporting part will be done by SCCM.
So as usual, as we all do, tried to find a guide on how to do this with MBAM and all. 😉I found several but almost all of them are outdated. With new MBAM 2.5 SP1, all you need is 2 additional steps in Task Sequence to enable BitLocker.
Please note that these are very basic task sequences just to give the core idea.
My environment:
- System Center Configuration Manager (Current Branch) 1610
- Microsoft Bitlocker Administration and Monitoring 2.5 SP1 with December 2016 package. (Integrated with SCCM)
- Windows 10 version 1511
- Windows 10 version 1607
- SaveWinPETpmOwnerAuth.wsf
- Invoke-MbamClientDeployment.ps1
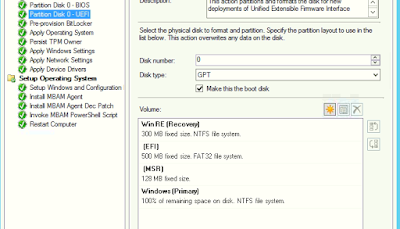
Type 1 - Pre-Provisioning BitLocker
To do this remove every BitLocker related steps in task sequence except for "Pre-Provision BitLocker". Create an additional system partition for BitLocker at least 300MB of size to store boot files.
After applying the Operating System, run the "SaveWinPETpmOwnerAuth.wsf" to retain the TPM owner authorization value. This value will save in MBAM database and can use for manage TPM remotely. Make sure to insert above step before the installation reboots into newly applied OS. Otherwise the value will not be retained
Note: Starting from Windows 10 version 1607, TPM owner value will not be retained. So if you need to manage TPM, you need a physical presence (TPM Owner Password). Even though Microsoft not recommend, still it is able to retain TPM owner password with editing a registry value.
After installing the MBAM Agent and December update patch to the MBAM Agent, time to run the "Invoke-MbamClientDeployment.ps1" to configure and record the key information to MBAM database. This is the hard part. Several parameters needed to run this Powershell script. Mandatory parameter is "-RecoveryServiceEndpoint" pointing MBAM server. But in my case I had to use the "-EncryptionMethod" parameter even it's optional. Value I used was XTSAES128, default encryption method of Windows 10, even though pre-provisioning already set the method. If i didn't use a encryption method or changed to a different method, script failed.
Also make sure MBAM BitLocker Group Policies are not applied to the OU which used in "Apply Network Settings" task sequence step. Because PS script gives errors if the GPOs are there. Best way is to use a OU that doesn't apply any BitLocker policies in join to a domain step and move the computer to the appropriate OU once the task sequence is completed.
Full line:
-RecoveryServiceEndpoint "http://mbamserver.domain.com/MBAMRecoveryAndHardwareService/CoreService.svc" -EncryptionMethod XTSAES128 -EncryptAndEscrowDataVolume -IgnoreEscrowOwnerAuthFailure -IgnoreReportStatusFailure
Above steps worked for me.
Type 2 - Full Disk Encryption






Hello,
ReplyDeleteI am trying to deploy Windows 10 1607 to our estate and save the TPM Owner information to MBAM. We require Fully Encrypt and I have followed the process above but it is not saving the TPM Owner. Is there anything else I need to do? What state should the TPM be in?
Any help much appreciated.
Thanks
Hi GF2013,
DeleteFrom Windows 10 1607 onward TPM owner info will not be retained. You need to have physical presence to manage the TPM. But still you can add some registry values and save TPM owner info.
Hi there,
ReplyDeleteGreat article. I have been trying to copy your TS but it hangs on the 'Invoke PowerShell Script' stage. How long should it take to get past this stage? Where can I find a log for this?
Your help is much appreciated. Keep the good work. :)
@Calvin go to C:\Windows\CCM\Logs and open the smsts.log log.
ReplyDeleteHi - Instead of Powershell script can we use the Enable Bitlocker TS step (SCCM 1702) ?
ReplyDeleteYes. Then your recovery keys will be stored in AD instead of MBAM DB.
DeleteThanks. I dont see the recovery keys in the MBAM DB. Have applied proper GPO settings and also run the PS1. What have to be checked ?
ReplyDeleteSorry. In my case the manage-bde always shows as :
ReplyDeleteitLocker Version : 2.0
Conversion Status: Used Space only Encrypted
Encryption Method: XTS-AES 256
Protection Status: Protection Off
Lock Status: Unlocked
Indentification Field: Unknown